Meeting the need for encryption and authentication in the IoT
IoT Security Part 3
The idea of leaving your home without securely locking the doors and windows may have been acceptable many years ago, and in some areas still is, but for the vast majority of homeowners it would be unthinkable; an unnecessary risk that leaves your home, your belongings and those things you value accessible to anyone.
As our homes become more connected, it has become necessary to think of those connected devices as doors and windows into our lives. Leaving them unlocked is, in many cases, the factory default setting and so it is now important that consumers and manufacturers understand the risk and the need for security in a connected world. It is easier than ever for the criminal element to exploit both literal and metaphorical open doors and windows, but there are steps that can be taken to make it more difficult for them and ensure greater protection for us.
Starting from a secure foundation
There are many things the user can do to make connected devices more secure, such as making sure encryption is selected for a wireless access point and that the default password is set. It is well known that routers and access points generally use a default IP address of 192.168.x.x, where x and x are (usually) either 0 or 1; it doesn’t take long to try all four combinations and if the administrator password is (still) admin, access is granted. Many manufacturers will make this clear in the documentation, but not everyone reads it. Often it is ease of use ‘out of the box’ that is cited for defaulting to no security, but perhaps this should change. The use of NFC for pairing is growing in popularity, as it allows keys and passwords to be securely exchanged, but it is unlikely to remove the need for at least some user interaction during installation.
Because wireless connectivity is now so prevalent it is easy to think this is the only way a device can be hacked and it is probably the most accessible, but it isn’t the only potential vulnerability. Physical hacking is a very real threat; if access to the device itself is possible it is often relatively simple to connect, physically, to a device and from there to a wider network. Manufacturers should consider restricting access to ports such as Ethernet, CAN, USB and JTAG in order to minimise this risk. Some microcontrollers now include anti-tamper detection features that warn of this type of attack, which should be managed at the software level.
Software is now, of course, a massive ‘attack surface’ for hackers. This is the term used to describe all of the ways in which a hacker could gain access to a system at the software level. The popularity of open source software is a double-edged sword in this respect; it allows developers to get to market quickly and at lower development cost, but any security vulnerabilities are inevitably known by the entire community. If open source software is used in a connected device, a process for facilitating over-the-air updates should also be included, to ensure any patches can be applied as soon as possible.
The value of data
The IoT and Big Data go hand in hand; the data generated by nodes provides a wealth of information that can be mined by cloud-based services to provide value in any number of sectors. As such, all data is not only valuable but critical, small changes to many data points from multiple devices could conceivably have long-ranging consequences. Subsequently it is important to ensure the data provided by IoT nodes is protected from cyber or physical tampering, which is most effectively achieved through encryption.
Data encryption involves encoding plain text into what is known as ciphertext. It requires a key to both encrypt and decrypt the plain text to/from ciphertext; if the same key is used it is referred to as a symmetric key scheme, but this requires both sides to have the same key and so exchanging the key becomes its own security issue. More common today is the use of public key encryption schemes, in which the encryption key is made public and only the decryption key is kept secret.
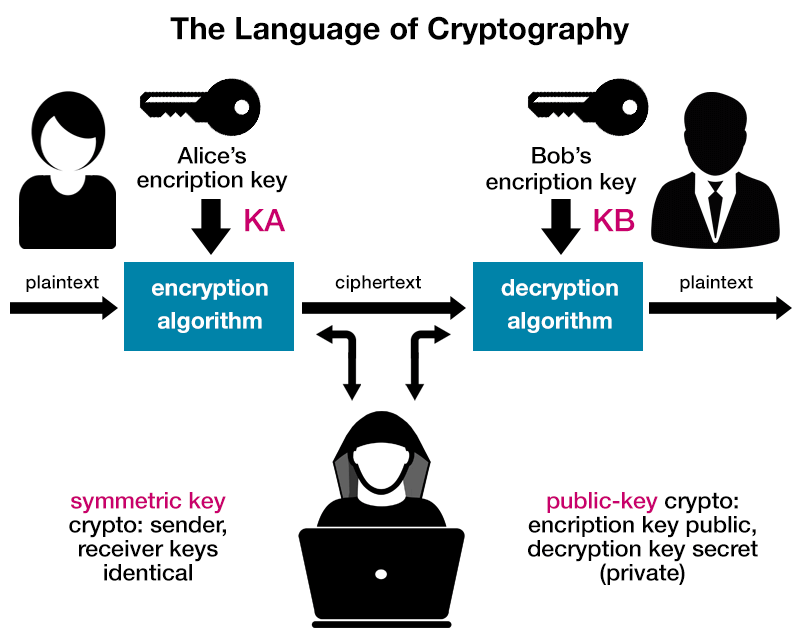
Figure 1. The language of cryptography - Image: ©Premier Farnell Ltd
Although manufacturers may focus more heavily on the secure exchange of data over a network, it is equally important to ensure data stored locally is also protected. Encryption can easily be implemented in an embedded IoT node to make data stored locally more secure, and the ciphertext can also be distributed over a network with confidence. Many microcontrollers now include hardware dedicated to accelerating the encryption process, which can be many times faster than performing the encryption process in software alone.
The most widely implemented forms of encryption include AES-128 (Advanced Encryption Standard, 128-bit), Data Encryption Standard (DES) and Triple DES (3DES). As DES uses a 56-bit key it is now considered too easily broken and has largely been superseded by 3DES, which effectively applies the encryption process three times. Each of these encryption algorithms employs reiterative functions which can consume many instruction cycles but, fortunately, are easily implemented in hardware. One example of a microcontroller that includes AES and DES accelerators, as well as tamper detection, is the TM4C129x family from Texas Instruments, which can be evaluated using the EK-TM4C1294XL board.
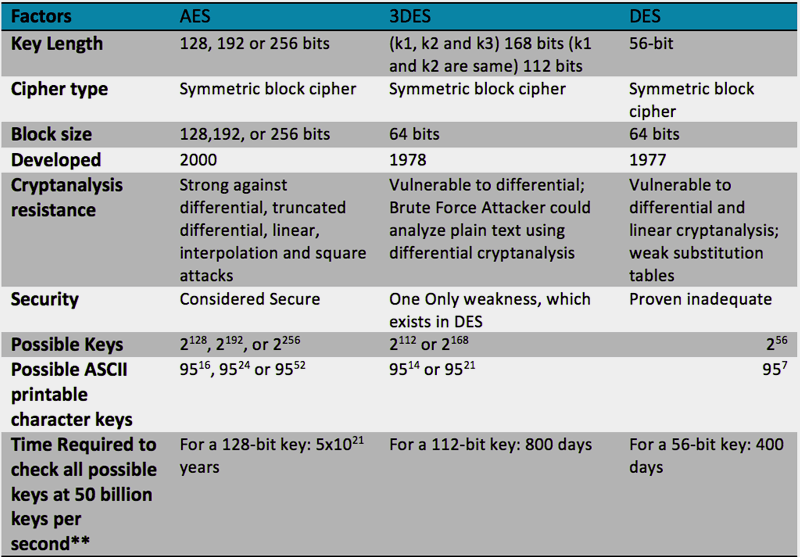
Figure 2. Comparison of AES, DED and Triple DES - Image: ©Premier Farnell Ltd
Authentication
Encrypting data before it is stored or exchanged can alleviate security issues but it isn’t without risk. Most wireless protocols include a level of encryption that can be implemented but, as outlined earlier, the default state is often no encryption. If an unauthorised device gains access to a network (through a man-in-the-middle attack, for example) it may be assumed that, as it is a part of the network, it is a trusted device and so is given access to decryption keys. Including some form of authentication that checks the credentials of a device as part of the network activity can prevent this from happening.
Protocols developed for the internet, such as HTTPS, support encryption and authentication between devices. However, as these are relatively complex protocols they can be difficult to implement in resource-constrained devices in the IoT. Also, authentication in the IoT isn’t quite so simple as it is across the wider web where people are involved; two-factor authentication is easier to instigate in a system when a keyboard, display and a person are present. Between two IoT nodes, authentication needs to be handled differently.
One way of authenticating devices is to issue each a username and password. The MQTT (Message Queue Telemetry Transport) is one of the most popular protocols used in the IoT and although it doesn’t feature encryption or authentication in its basic form it does provide support for both. This includes authentication with a username and password, an access token or a one-time password, as well as certificate-based authentication.
Other protocols targeting the IoT, such as CoAP (Constrained Application Protocol), have been developed to support the IoT and therefore address the known security issues such as encryption and authentication, while understanding that the resources (compute performance, power) of the device may not be able to support large code or complex algorithms.
Ultimately, encryption and authentication need to work hand-in-hand in order to deliver the best results. New developments make that possible, even for devices with limited resources.
Maintaining a secure system
Protecting data extends to the intellectual property inside the device, in the form of the hardware design and the embedded software. Increasingly, semiconductor manufacturers appreciate how important this is and provide techniques to secure both. Firmware is particularly at risk. Having access to the firmware in a device would allow a subcontracted manufacturer to overproduce a device for their own financial gain, for example. Making firmware totally inaccessible also has implications, however. It is common, as mentioned earlier, to update firmware after a device has been shipped; so called over-the-air updates. These are useful for patching security holes in open source software, but they are equally useful for manufacturers to address any bugs the product may have shipped with. Securing firmware that has to be updated can be difficult, but there are solutions and, again, it relies on implementing encrypting and authentication techniques. In this instance the encryption might be applied to the firmware, which can only be decrypted with the right key.
If physical access is possible, hackers can attempt to replace the embedded firmware with a version that provides them with network access. To protect against this, methods to establish a ‘root of trust’ between the processor and the internal/external memory have emerged. One such method is hashing, which is essentially very similar to a checksum. This is derived from the data itself and so if any of the data (or program code) has been changed since the checksum was calculated, it will change the result. This form of authentication is now commonly used in embedded processors that provide ’secure boot’, and the same technique can be applied to over-the-air updates.
As all cryptographic techniques rely on keys being kept secure manufacturers now offer devices dedicated to the task, such as the DeepCover range from Maxim Integrated. This includes the MAXQ1061 cryptographic controller, which provides key generation and storage, digital signature generation and verification, and packet encryption, as well as being a secure boot loader for a host processor. The device can be evaluated using the MAXQ1061-KIT#.
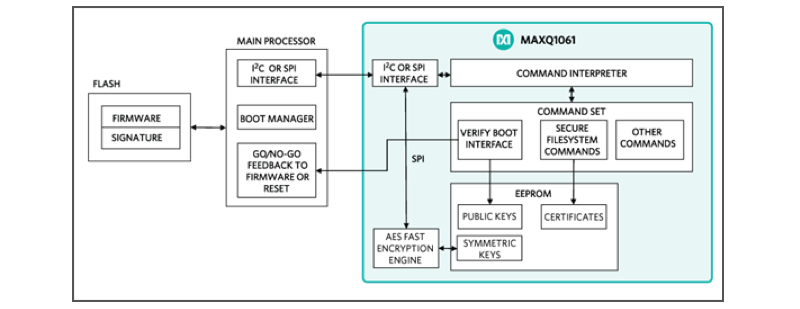
Figure 3. Block Diagram of MAXQ1061 – Copyright Maxim Integrated Products (http://www.maximintegrated.com). Used by permission.
Conclusions
The IoT is changing the infrastructure of modern life, its influence will be felt in every industry and every sector. Security has always been high on the agenda for companies targeting the IoT and its many applications, as well as the developers who need the resources to help ensure they can deliver products that will meet their customers’ requirements.
With the need for cryptography in embedded devices rising, semiconductor manufacturers are now meeting that demand with innovative solutions that will ensure the IoT meets and probably exceeds its expectations.
Meeting the need for encryption and authentication in the IoT. Date published: 29th August 2017 by Farnell element14