3 Key Questions You May Be Asking Yourself About The Industrial Internet of Things
You’ve probably heard the advice that’s being given around the manufacturing industry today: Manufacturers must eagerly adopt technological innovation to improve productivity to remain competitive. This is why the Industry 4.0 initiative and the Internet of Things (IoT) has drawn the industry’s attention to the benefits of the data-driven enterprise. Expect manufacturing facilities to experience a seismic transformation in the coming years. Yet, big leaps in change can cause confusion or even inaction. To simplify what these changes mean and how to prepare for them, element14 has invited Jeff Lund, Belden’s Senior Director of Product Line Management – Industrial IT for a Q&A on to address some of the key questions that you be asking yourself about the Industrial Internet of Things and what you should do to prepare.
element14: One of the big drivers I hear about for the Industrial Internet of Things is enabling manufacturing decision makers to gain visibility to current factory conditions from anywhere –the office, off-site, or on-the-go while walking the factory floor. To me this sounds like an immensely complex system from sensor to controller to gateway to cloud to mobile. Should I work on these all at the same time or in stages?
Jeff Lund: When thinking about the Industrial Internet of Things (IIoT), it is easy to become overwhelmed by all that you don’t know – what new devices will you add, what new data will you generate, what new applications will consume all this data. But if you step back and think about it, while you don’t know all the details of what the future holds, you do know enough today to take the right steps to prepare.
In particular, you know three key things – there will be more and more devices that attach to your standards-based industrial Ethernet network over time, those devices will be generating more and more data, and that data will be used by more and more applications. To support this future, you need a network that is well architected and well secured.
2. Belden has created a simple 5 step process to help guide you through the process of assessing the network infrastructure you have today and developing a plan to update and enhance it to be prepared for the future – whatever it holds.
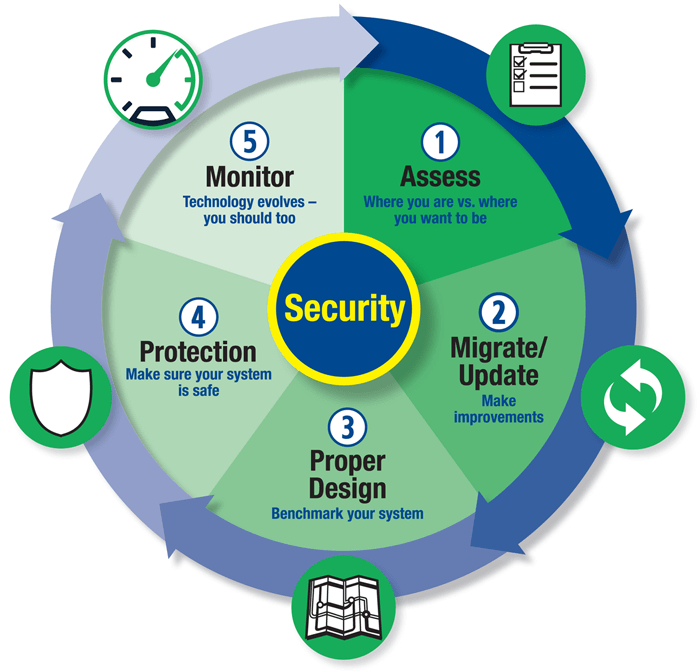
- Assess and Map Industrial Networking Infrastructure. Before you start to enhance your system, you need to understand what you already have. What are the connectivity (wired/wireless, bandwidth, reliability) and environmental requirements of current systems? What are the near-term goals in terms of functionality and data exchange? The end result of the assessment stage should be an accurate ‘map’ of your network’s infrastructure.
- Migrate / Update to Ethernet. The IIoT is built on industrial-hardened versions of the technologies that power the Internet. You’ll want Ethernet (wired and wireless) to be the foundation of your communications infrastructure, so for existing components – such as sensors, actuators and electric motors – that communicate using fieldbus, plan their migration to Ethernet.
- Update Network Design to Meet Best Practices. This step is where we recommend you pause to make sure your program meets established best practices and standards. Belden and its partners offer resources that can help in this process.
- Enhance Reliability and Resiliency with Defense in Depth. Cybersecurity has become a bigger and bigger challenge in industrial environments – and it isn’t just about protecting against attacks by hackers. The majority of industrial cybersecurity incidents are unintentional, resulting from human error, device flaws and accidental malware introductions. The IIoT, with its more-things-connecting-in-more-ways, only makes the cybersecurity challenge more important.
- Monitor for Changes. The last step is a feedback loop into the first. Technology is constantly changing. Security threats are changing. Business needs are changing. You need to monitor all of these things and make changes to your systems accordingly.
element14: Most manufacturing plants already collect a lot of data in their production processes. If what we know about Industrial IoT is true, plants will be collecting plenty more. But to collect all this data, the devices (i.e., sensors and actuators) need to be digitized and interconnected. How does a manufacturing plant making sure all of its devices are ready for Industrial IoT?
3. Jeff Lund: One important thing to keep in mind for the IIoT is that does not require you to “rip and replace” what you already have. The value comes from migrating to a standard networking infrastructure (industrial Ethernet) and then integrating data from devices into business applications. While you may be thinking that the most important issue to consider is how to get the data out of your devices and into business applications, I would argue that it is not. That is not to say that gaining access to data is always easy – you may need to upgrade your network infrastructure to be better segmented and run at higher speeds to support the additional data flow and you may require gateways to integrate existing devices (fieldbus, serial, IO-Link, etc.) into your IIoT solution – but there are many people that can help you down this path. To me, the more critical, and more often overlooked issue, is how to ensure the reliability, resiliency and security of your systems as you connect all these devices. Part of this comes from following good network design practices, but that is not enough.
As I said at the start of this answer, a very important of the value proposition of the IIoT is enabling you to gain greater value out of devices you already own. These devices were designed with the idea that they would be used in well structured, closed systems. As such, most protocols in use in industrial systems today have no built-in security. The devices often have been tested under condition of how well they behave under proper conditions and those can fail when exposed to malformed packets or excess traffic. A high percentage of devices vulnerability security alerts reported through the Department of Homeland Security fall in to this camp. And of course these existing devices were never designed with the thought that they’d be connected and exposed to corporate networks or the Internet where they might be subject to unintentional traffic or intentional attack.
So, one critical step to preparing your devices to be ready for the IIoT is to enhance their security, not only to protect them from attack but more importantly to ensure that your network remains reliable and resilient. The ISA/IEC 62443 Cybersecurity is a good starting point for guidance on how to access and enhance your system design. Special purpose security appliances such as the Tofino Xenon® enable you to easily implement ISA/IEC 62443 “zones and conduits” into your system and lock down communication to your existing devices to ensure proper traffic flow.
element14: If there is one thing that appears to be major obstacle to the adoption of the industrial Internet of Things is adequate security. How can I prepare my facility for a secure industrial IoT?
Jeff Lund: If you’re worried about security, you’re not alone. Surveys of executives and business decision makers often report security in the top one or two concerns that they have about the IIoT. They are typically very exciting about the business benefits they see and almost equally concerned about the business risks that IIoT done poorly could have on their operations.
The good news is there are lots of resources you can turn to for help. For example, the Industrial Internet Consortium, a global organization of over 200 companies and organizations that promotes the accelerated growth of the Industrial Internet of Things, where I am the marketing co-chair, has recently published Industrial Internet Security Framework Technical Report with best practices guidance. Likewise organizations list NIST and SANS have also published Industrial Internet security recommendations. Belden has also developed a simple “1-2-3” approach to help you assess where you are and take simple, concrete steps to enhance your system’s security.
However, before you begin any changes to your system, is to start with a risk and vulnerability assessment. Once you know what are your most important assets and biggest risks you can prioritize what to protect first and develop a plan.
Click here to join in the discussion on how to prepare your network infrastructure of the Industrial Internet of Things